Authenticate RCE in some Huawei Products
RCE issues are found in B2368-57
CVE-2020-9199
CVSS 6.8 (AV:A/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H)
Time line
- Discovered 26/07/2020
- Reported 26/07/2020
- Fixed and Release 02/09/2020
An attacker need obtain user account information before exploiting this vulnerability
Affected devices
| Version | Software | Firmware |
| B2368-57 | B2368_V100R001C00SPC114 | 11.620.XX.XX.XX |
Sumary
SSRF to RCE issues are found in B2368-57 changing the default endpoint to a false one and bypassing software validation check, injecting os command, because use directly wget OS command, to obtain a new firmware.
First
you must change the default endpoint to a fake one.
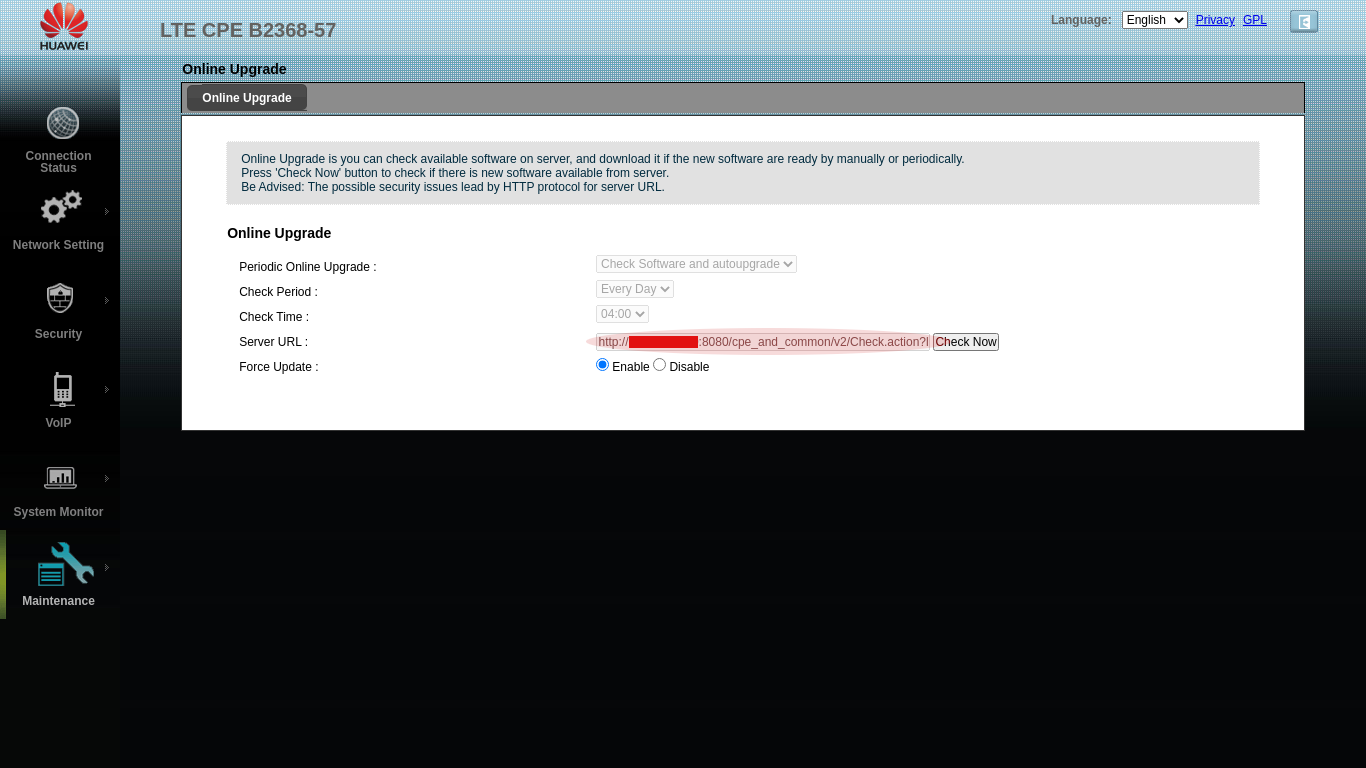
Remote fake endpoint
In this case is possible show the full domain and port used for the ISP.
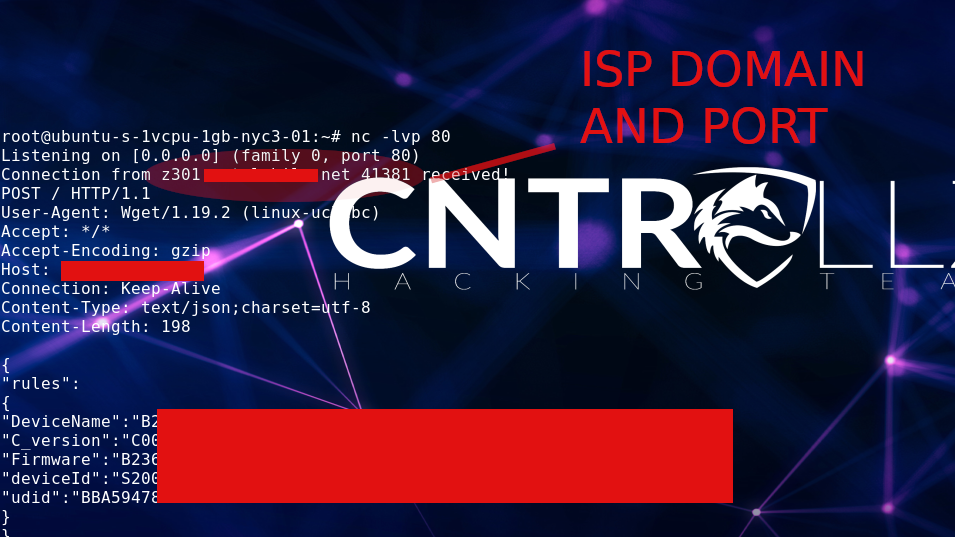
You can bypass url with # and change wrapper http:// to ftp://
RCE
Is possible bypass the sanity check in Wget command. Yes! is possible you need mount a fake endpoint, in this case im use flask to host the payload with os command.
Then
you must accept and download the fake firmware.
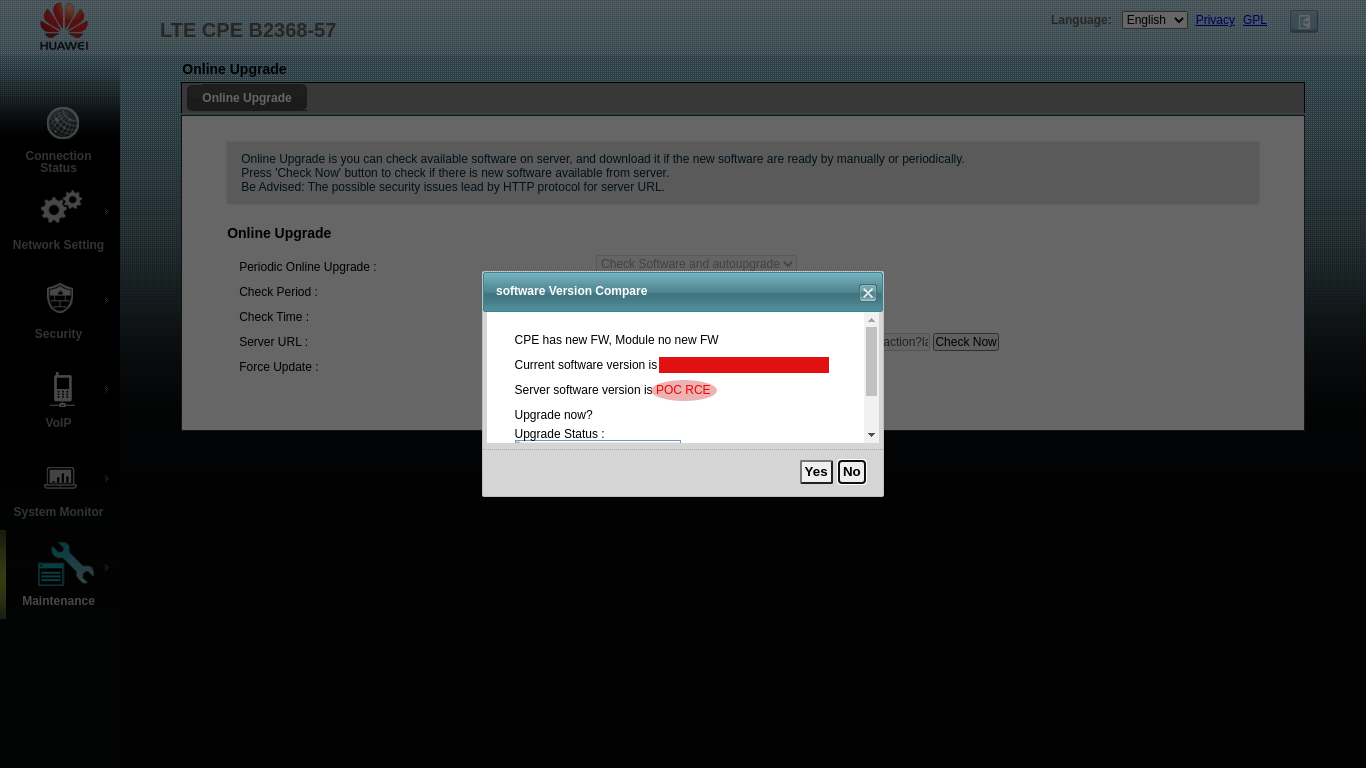
Got RCE!
you can execute OS command. 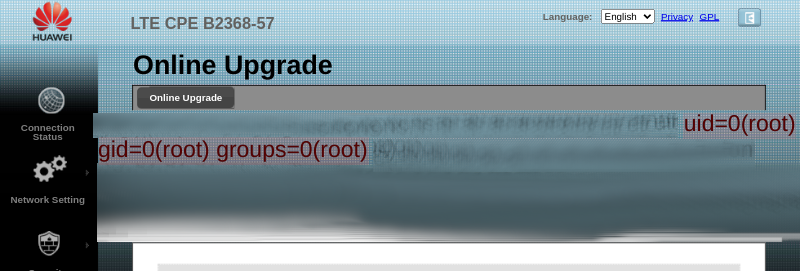

How this work?
After accepting the malicious firmware download, the basic software package file validity check be bypassed and inject command to execute in the B2368-57 device.
Impact
- Successful exploit of the vulnerability will cause the target device be controlled.
Demo exploit
 Reported to Huawei Psirt Regards Mataya
Reported to Huawei Psirt Regards Mataya